Research on RFID Security and Privacy Protection Solutions
 2021-12-03 14:59
2021-12-03 14:59

RFID is a contactless automatic identification technology that emerged in the 1990s. Its wireless communication method and non-visible read and write requirements have brought us great convenience and also many security and privacy concerns. In view of the security and privacy issues of RFID, a lot of research has been carried out to strengthen RFID security and privacy protection at home and abroad, and a number of methods have been proposed, such as Hash Lock, Random Hash Lock and Hash. chain, but these methods are neither safe nor efficient Low-level defects. In view of the shortcomings of existing methods, this document takes a closer look at the security and privacy protection of RFID.
1 RFID technology and its security and privacy analysis
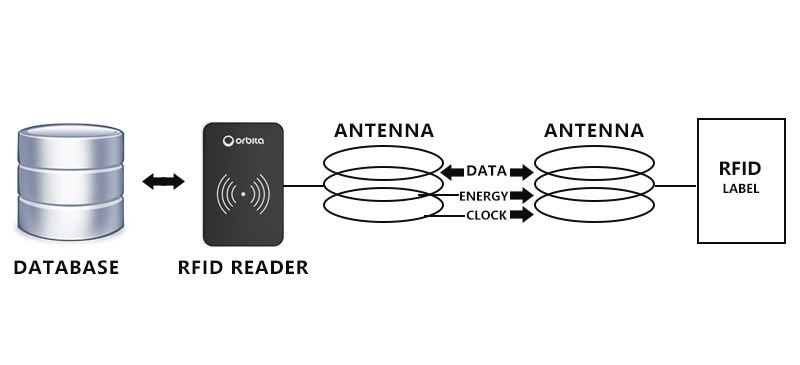
The RFID system is mainly made up of readers, tags, and back-end databases, as shown in Figure 1.
1 RFID technology and its security and privacy analysis
The RFID system is mainly made up of readers, tags, and back-end databases, as shown in Figure 1.

At present, RFID technology has increasingly attracted the attention of industry and academia, and has been widely used in supply chain management, access control, e-wallets and other occasions. However, RFID technology is a contactless automatic identification technology, and the main security and privacy threats it faces are:
(1) Illegal reading. Commercial competitors can quickly read supermarket product label data through unauthorized readers to obtain important commercial information;
(2) Position tracking. Through RFID tag scanning, the location of consumers can be tracked and located according to the specific output of the tag;
(3) You eavesdrop. Because the RFID system has a long signal transmission distance on the forward channel, intruders can easily steal the signal data sent by the reader;
(4) Denial of service. Man-made signal interference prevents legal readers from reading tag data normally;
(5) Pretend to cheat. Disguise yourself as a legal label to mislead the reader into providing incorrect information;
(6) Repeat. According to the data communication between the spied reader and the tag, the above communication behavior is repeated to obtain the data information.
2 RFID security privacy protection
RFID privacy and security issues hinder further promotion of RFID technology and attract great attention from consumers.It is extremely important to strengthen RFID security and privacy protection.
2.1 Prerequisites and requirements
The communication between the reader and the backend database is supposed to take place on a secure and reliable connected channel, but the wireless communication between the reader and the tag is easily heard. To popularize RFID technology, it is necessary to ensure the low-cost implementation of RFID tags.
Since the calculation required by the standard security mechanism is more complicated, for example, SHA-1 requires about 12K gates, which cannot be achieved in low-cost tags, so low-cost one-way hash functions can be use for encryption.
A secure RFID system must be able to withstand various attacks and, taking into account the worst situation, even if external persons obtain the secret data inside the tag, you must ensure that you cannot trace the historical activity information related to the tag, i.e. , to ensure forward safety.
2.2 Typical method
Typical access control methods to strengthen RFID security and privacy protection mainly include Hash blocking, Random Hash blocking, and Hash chain, all implemented based on one-way Hash functions.
2.2.1 Hash Lock (Hash Lock)
The Hash lock method is used to control the tag read access, and its working mechanism is as follows
IMG
IMG
Lock tag: For a tag with a unique identification number ID, the reader first randomly generates the tag key, calculates metaID = Hash (key), and sends the metaID to the tag; the tag stores the metaID and enters the locked state. Reader stores (metaID, key, ID) in backend database and uses metaID as index.
Unlock the tag: when the reader requests the tag, the tag responds the metaID; the reader consults the backend database, finds the corresponding record (metaID, key, ID) and then sends the key value to the tag; After the tag receives the key value, it calculates the Hash (key) value and compares it to the metaID value stored in itself. If Hash (key) = metaID, the tag sends its ID to the reader. At this time, the tag enters the unlocked state and opens all functions for nearby readers, as shown in Figure 2.
Advantages of the method: The One-Way Hash function is more difficult to crack, so this method can prevent unauthorized readers from reading the tag information data, and to some extent provide privacy protection for the tag; This method should only be implemented to Hash in the tag. The calculation of the function, as well as the increase in the storage of the metaID value, are therefore easy to implement in low-cost tags.
Method flaws: Since the data answered by the tag is specific during each query, it cannot prevent location-tracking attacks; the data transmitted by the reader and the tag is not encrypted, and spies can easily obtain the key and identification values of the tag.
2.2.2 Random Hash Blocking (Random Hash Blocking)
To solve the problem of position tracking in Hash lock, Hash lock method is improved and random Hash lock method is adopted. First enter the string connection symbol ", as the tag ID connection, and the random number R is represented as" IDIIR. "In this method, the database stores the ID value of each tag, set as ID1, ID2? IDk? IDENTIFICATION.
Lock Tag: You can lock the tag by sending a simple lock command to the unlocked tag.
IMG
IMG
Unlock the tag: the reader sends a query to the tag ID, the tag generates a random number R, calculates Hash (IDIIR) and transmits the data pair (R, Hash (IDIIR)) to the reader; after the reader receives the data pair, get all tag ID values in backend database, calculate each Hash (IDIIR) value and compare it to received Hash (IDIIR), if Hash (IDk 『 JR) = Hash (ID 』JR), send it to tag IDk; if the IDk received by tag = ID, the tag is unlocked at this time, as shown in Figure 3.
In this method, each response from the tag is random, so you can prevent location-tracking attacks based on specific results. However, this method also has certain drawbacks: (1) The reader must look up all tag IDs and calculate the Hash (IDkIIR) for each tag. Therefore, when the number of labels is large, the system delay will be very long and the efficiency is not high; (2) Random hash lock has no forward security. If the enemy gets the Tag ID value, the Hash (IDIIR) value can be calculated based on the R value, so the historical location information of the tag can be traced.